cybersecurity
Spoofing a website: what is it and how does it function?
Learn what website spoofing is, how it is done, and its potential harmful applications. Find out how you can protect yourself from this type of cyber attack.
Telephone Hacking – Tips on how to Remove A Hacker
It has become a growing difficulty to protect oneself from cyber attacks. Cybercriminals are becoming more superior and cellular, rendering it difficult to track and prevent them. Many many people turn to telephone hacking as a last resort in order to remove hackers from their particular devices. However, this process is not really easy and…
Cybersecurity-as-a-Service with New AI-Powered Solution Introduced
—
in Latest NewsThis article is intended for the readers to provide knowledge on the new AI-Powered Cybersecurity-as-a-Service. We will also adhere to concepts like what CSaaS is, its benefits, and incorporating AI into cybersecurity. Learn the essential skills required to master cybersecurity by accrediting the certification with this online Cybersecurity Training course. Networks of Vector Security® declared…
Cybersecurity Vs Data Science
—
in Latest NewsCybersecurity and data science are two very important fields of study. They are both necessary in order to keep our online presence safe and protect our data. Cybersecurity is the practice of protecting computer systems from unauthorized access, use, or disclosure. Data science is the application of statistics, mathematics, and other quantitative methods to analyze…
6 Web Hosting Security Features You Should Not Overlook
—
in SEO TipsThe very fact that your site is exposed to the world means that it could be an easy target for hackers. Once compromised, it could lead to hacking and data leaks, which are no good at all. It could cause your rankings and reputation to suffer. To keep your website information secure, you should consider…
10 Steps to Cybersecurity with IASME Certification
—
in ComputerWith IASME certification, you can lead your business in the right direction with the right level of security. However, most of the people are still unaware of how they can implement cybersecurity with IASME certification. If you are one of them, let’s look at the following official ten steps to ensure cybersecurity with IASME certification:…
Symantec Integrated Cyber Defense Exchange Helps to Simplify Integrations Across Symantec Portfolio and Partner Ecosystem
—
in SoftwareSymantec Corp ., a global leader in cybersecurity, today announced the general availability of Symantec Integrated Cyber Defense Exchange, a free software solution that simplifies integrations between Symantec products and a broad range of popular partner products. Customers need to reduce complexity related to integrations, event data and workflows across the Symantec portfolio and third-party…
How To Parental Control App Help to Keep Bullies off Kids Phones
Cyberworld – The new playground for bullies! Bullying is an abnormal, often aggressive behavior towards a soft target. Bullies can be physical or verbal, visible or invisible, and violent or silent predators. Cybercrime is a common term in today’s technological world; bullying is just another less violent crime adopted by kids in the online world.…
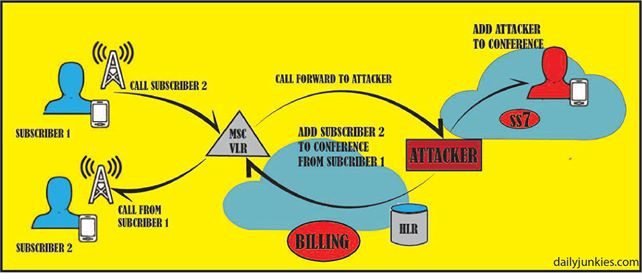
Man in the middle attack
—
in Latest NewsInternet has become an indelible part of our lives. We can’t really imagine a day without an internet device in our hands. It can be synonymous to oxygen now, we breathe internet, we sustain on it. With the course of time, it has become more accessible and affordable and therefore, everything has become digitized. Since,…
MIT faculty approves new urban science major
Urban settlements and technology around the world are co-evolving as flows of population, finance, and politics are reshaping the very identity of cities and nations. Rapid and profound changes are driven by pervasive sensing, the growth and availability of continuous data streams, advanced analytics, interactive communications and social networks, and distributed intelligence. At MIT, urban…
BMT Named a Top Cybersecurity Firm in New Jersey for Second Consecutive Year
—
in ComputerBusiness Machine Technologies, Inc. (BMT) is excited to announce that the company has been named one of the top Cybersecurity Firms in New Jersey…. Computers – United States – Latest News
Egan-Jones Recommends “withhold” Vote From Adobe Board Chairman Because of Cybersecurity Issues
—
in ComputerHaverford, PA – Egan Jones Proxy Services (EJP) released a report calling for a “withhold” vote for the Board Chair of Adobe Systems Incorporated [ADBE], Shantanu Narayen, due to a poor Cybersecurity Rating and Board Rating…. Computers – United States – Latest News